Time-Based OTP: Configuration and Verification
A two-factor authentication (2FA) technique called a Time-Based One-Time Password (TOTP) creates a password that is only good for a brief amount of time, usually 30 seconds. To add an additional degree of protection, it is frequently used in combination with other authentication methods, including a username and password.
How does TOTP work?
- Shared Secret Key: The user and the authentication server share a secret key (often generated during account setup). This key is stored securely on both the client (e.g., in a mobile app like Google Authenticator or Authy) and the server.
- Current Time: TOTP relies on the current time (usually in UTC) and divides it into time intervals (e.g., 30 seconds). Each time interval has a unique number, which is used in the OTP generation process.
- OTP Generation
- A cryptographic function (HMAC-SHA1 or similar) combines the secret key and the current time interval number.
- This produces a hash that is then truncated to generate a 6-8 digit code.
- OTP Validity: The OTP is only valid for a short period (usually 30 seconds). Once the time expires, the code becomes invalid, and a new code is generated.
- Authentication
- The user enters the OTP shown in their authentication app.
- The server also calculates the OTP based on the shared secret key and the current time.
- If the OTP entered by the user matches the one calculated by the server (within a certain tolerance window), authentication is successful.
- Syncing: Both the client and server must be synchronized at the same time. If there is a significant time drift between them, the OTP may not match, leading to authentication failure.
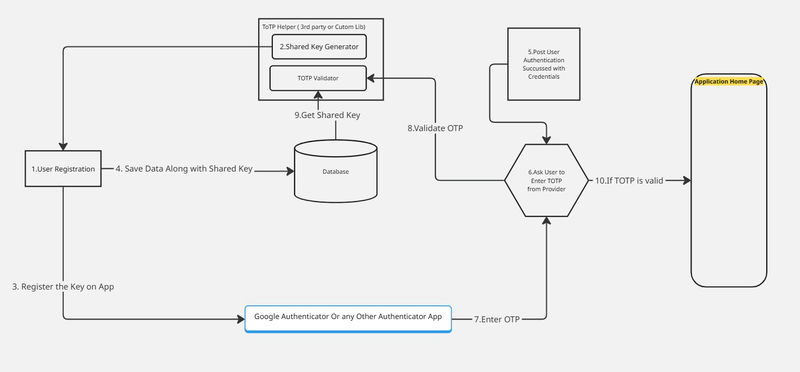
Flowchart
I have represented each step in the flowchart below.
Implementation
Let’s Try To understand the implementation with C#.
There are 2 ways to implement the TOTP logic (Generate a Sharable Key and validate the TOTP).
- Create your Custom Logic
OR - Use existing Libraries
Since our main goal here is to enable TOTP for Application, I will be using the existing Open-source Library.
Otp.net
I am using Otp.net to implement the functionality. Let’s see step by step approach.
Reference Otp.net
Add the Otp.net package to the project
Generate Secret
As the initial step in implementation, generate the Secret Key, which will be used to create and validate the OTP.
Convert Secret to QR code for Authenticator Apps
As we need a QR code of the above generated Secret to register on the Authenticator app, use an online resource to convert a secret into a QR code.
Now register it on Google authenticator
Validate OTP
Here is the code to validate the OTP
Note. We should store the secret in the Database against the User to send it for validation.
ASP.NET Core 8.0.11 Hosting Recommendation
HostForLIFE.eu
HostForLIFE.eu is a popular recommendation that offers various hosting choices. Starting from shared hosting to dedicated servers, you will find options fit for beginners and popular websites. It offers various hosting choices if you want to scale up. Also, you get flexible billing plans where you can choose to purchase a subscription even for one or six months.

